This blog will have multiple parts. I will introduce my view of a data protection reference architecture and the next few blog posts will talk to components of that architecture.
The other day I had a very interesting conversation with a colleague of mine in Australia. He was looking for a data protection reference architecture that he could use to speak to his customer. As you can imagine having this conversation over the phone could pose to be a difficult challenge. When the conversation began, my fear was he was looking for an ‘architecture’ diagram that included data protection appliances, backup servers, disk libraries, tape libraries and backup agents. I quickly realized that this is an impossible conversation to have with him without knowing:
A) the customer’s environment or challenges
B) the customer’s business objectives
I find that most vendors don’t know A or B when speaking to a customer about their data protection ‘issues’, but they really should. Having a more thoughtful conversation with customers in a consultative fashion is more relevant to customers in understanding their challenges and helping to align these challenges to the best possible solution.
I started my conversation with the diagram shown below (Figure 1). A simple triangle divided horizontally into 4 segments and the middle two segments divided vertically in half. Each segment represents different business objectives within a company. As you go around the triangle, you can see that there are different technologies and different methodologies for attacking data protection challenges, which is why there is no longer a “one size fits all” approach when it comes to protecting data today. Let’s face it; the two most important commodities in backup are time and capacity. One of the primary drivers behind the type of protection that is used is the Recovery Point Objective or RPO. Different technologies provide different RPOs and each has a different price point as well as there are different processes that can be applied to attach RPOs.
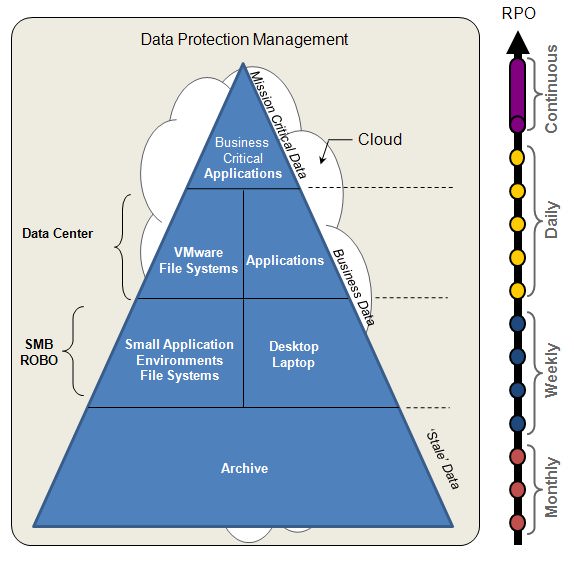
Having a conversation specific to this diagram can have a tremendous amount of value on a number of fronts, including; aligning technology needs with business objectives as well as highlighting critical pain points and beginning a roadmap that helps implement data protection technology based on business needs and budget and put you on the Road to Recovery.
The next post will cover the foundation of the triangle – Archive.