A couple of my colleagues went to New York and got to ring the closing bell as a part of the National Cybersecurity Alliance for which we (Dell Technologies) are a sponsor. While there they had a day of panels and other sessions they could listen in on to hear what is the latest with cybersecurity.
A BIG take away the team had from the event was the lack of mention of “Zero Trust”. In fact, the team said that because it was not mentioned was what made it so obvious that it was a bit strange.
The notion that Zero Trust is waning in popularity isn’t strange. It happens all the time in the tech world, what is hot one day is cold the next. There are a few reasons. First, a year ago security was the “most important thing” and providing a name around it, like Zero Trust, made it cool. Every vendor wanted to be a Zero Trust company. The hot thing today is GenAI. Everyone wants to be a GenAI company. Also, in 2022 the White House came out with Executive Order on Improving the Nations Cybersecurity saying companies needed to adhere to the 152 activities (page 19) that the DoD defined as Zero Trust. Now as time has moved forward, there are a lot of companies that believe they don’t need to do that. In addition, there have been some concerns about what the real definition of Zero Trust is. Dell hosted a LinkedIn Live where one of the guests was Theresa Payton, who was named the first-ever female White House Chief Information Officer said in our pre-call “she really didn’t like term Zero Trust but more Zero Trust ….”
Last year Dell discussed Zero Trust with a customer, who had been impacted by a cyber attack, and asked them, “are you planning on implementing a Zero Trust architecture?” and they basically said “no”. To them it wasn’t about all of the activities around Zero Trust, but they wanted to implement ways to make their perimeter more secure. In addition, this company’s perimeter was made up of over 500,000 IoT devices and they were not clear on how Zero Trust would help that environment.
Just yesterday I presented Dell’s position on cybersecurity to a number of customers from Argentina and during this presentation I asked all of them, “What do you think of when you think of Zero Trust?”. One of the customers CISO responded and said its more of a mindset. To them it was more about the ability to make their infrastructure more secure by ensuring the right level of trust was given to the right people to access the tools they needed to get their job done efficiently and no more.
In both cases what these customers were looking to implement was something along the lines of perimeter less security. A large percentage of the customers I talked to believe that Zero Trust is really about better perimeter access. Customers want to reduce the reliance of VPNs or a wall to keep the threat actors out and more of a system where each individual that needed to come in, is provided with the right credentials to be able to access what they need and that is all. If a user doesn’t have the right credentials, then they wouldn’t be allowed into the environment.
The reality is this is not what the true definition of Zero Trust is. Zero Trust is a foundation of 45 capabilities that does include capabilities around identity access management (IAM) but also things around network segmentation, encryption, machine learning and artificial intelligence, reporting, and automation to name a few (see figure 1)
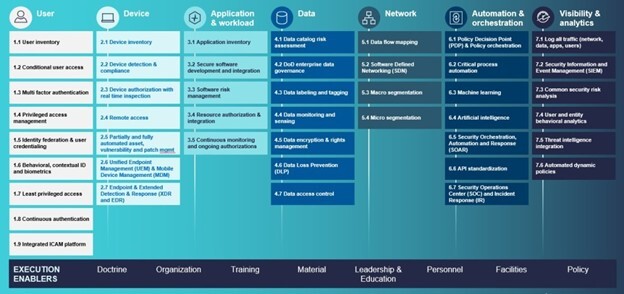
I would also bet that when customers are answering questions in surveys such as this Forrester survey about Zero Trust, most are not thinking about the 45 necessary capabilities but more the core capabilities of protecting the perimeter of their environment.
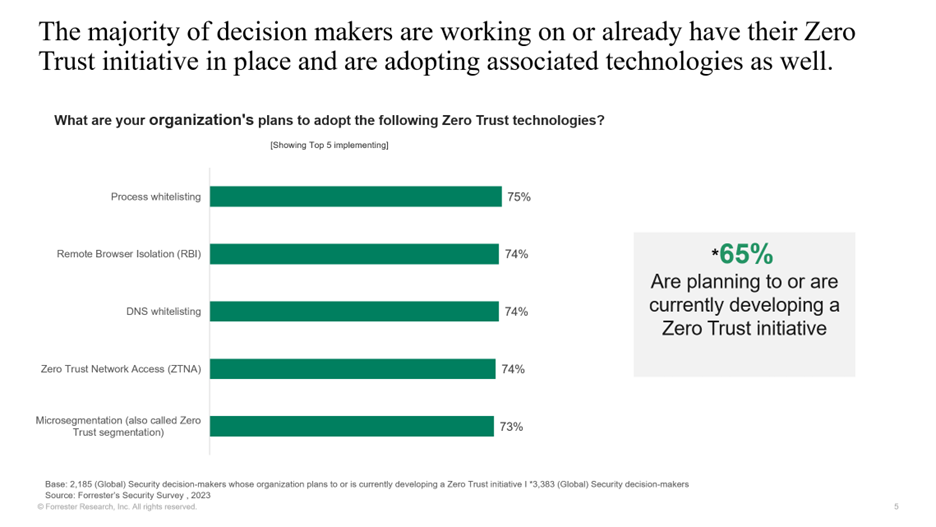
Two of the top 3 items called when organizations were asked about what their organizations were doing to adopt Zero Trust, they were going through a process know as whitelisting. A whitelist is a strategy IT uses that approves a list of email addresses, IP addresses, domain names or applications. In the past, customers used to create “blacklists”, these are email addresses, IP addresses, domain names, that aren’t allowed into the environment and everything else had access. The “whitelist” is the opposite. These are email addresses, IP addresses, domain names that can come in and everything else is blocked. This really is a much more secure way of knowing who can get access to what in your environment.
Now that we know what customers as really and truly asking for, what are somethings that can help customers with advancing their cybersecurity maturity when it comes to their perimeter? As we just pointed out, whitelisting is a great way to get a handle on who can come into the environment. In addition, taking advantage of multifactor authentication is a great first step in stopping threat actors from getting into the environment. Taking advantage of technologies such as roles-based access controls or RBAC can also help. If the user doesn’t have a role, they can be kicked out of the environment. Utilizing solutions such as dual authentication. This is the equivalent of needing two keys to launch the nuclear missiles (think the War Games movie 1983). If someone wants to do something, especially if it is a sensitive command, two people need to ratify the action, this provides some checks and balances. Not all solutions have this capability, but as customers look for more secure solutions for their environment, they should be considering looking for these types of capabilities.
This isn’t to say that the other capabilities for Zero Trust aren’t important when advancing your cybersecurity maturity, they are and should be implemented. But if your definition of “Zero Trust” is really more about reducing your attack surface, these capabilities are some really great first steps.
